Skip to main contentIntroduction
Ekho takes fraud extremely seriously, and has invested in rigorous fraud detection and prevention mechanisms to shield dealers and lenders from fraud. Our goal is to catch and block fraudulent buyers before they even submit a financing application. This document explains how Ekho’s multi-layered fraud prevention works, from advanced AI-driven screening to manual reviews and final verifications.
Ekho’s Fraud Prevention Overview
Ekho safeguards dealers and lenders by integrating advanced fraud detection and smart operational controls into every transaction. Our systems use the same models trusted by top auto retailers like CarMax, screening every buyer through a multi-layered process:
- Risk Scoring: Buyer data (device, network, identity, etc.) is analyzed in real time using sophisticated fraud software trained on extensive industry data. Risky behavior is flagged immediately.
- Verified Payments: We only support secure, fraud-resistant methods. For example, ACH payments are vendor-guaranteed and non-reversible, and we verify that the payment account belongs to the buyer.
- ID Verification: Every buyer uploads a government-issued ID, which we validate against national registries to detect fakes, alterations, or mismatches.
- Comprehensive KYC: We confirm identity details beyond ID, including email, phone, and when applicable, SSN – using data enrichment to flag stolen or synthetic identities.
- Multi-Factor Authentication: If risk is detected, we require added verification (e.g. one-time passcodes or selfie ID match) before allowing buyers to proceed.
- Manual Review: Ekho’s fraud analysts manually review all flagged cases. Transactions don’t proceed unless fully verified, which sometimes means getting on a video call with the customer.
- Dealer Visibility: Dealers get access to buyer documents and verification results before delivery, enabling a final ID match at handoff. Our support team is always available to help.
Multi-Layered Fraud Detection Approach
 Ekho’s fraud detection is methodical and multi-layered—we check several facets of a buyer’s information and behavior in parallel. Below are the key elements of our process and how each works:
Ekho’s fraud detection is methodical and multi-layered—we check several facets of a buyer’s information and behavior in parallel. Below are the key elements of our process and how each works:
Device & Behavioral Biometrics
Every interaction a buyer has with Ekho’s online checkout is quietly analyzed for consistency and legitimacy. We collect device intelligence – information about the buyer’s device and network – and behavioral biometrics, which is how the buyer interacts with our site. This entails:
- Device Fingerprinting: We collect data like device type, OS, browser, IP address, and geolocation to create a unique device “fingerprint.” If a known fraudulent device reappears—like one used in a past scam—our system flags it.
- VPN/Proxy/Emulator Detection: We detect if a buyer is masking their identity using a VPN, proxy server, or virtual machine—common fraud tactics to spoof location or simulate a fake device.
- Behavioral Analysis: We observe how buyers fill out forms and navigate. Normal users type and click at natural speeds, while fraudsters may autofill or paste stolen info quickly. We analyze typing rhythm, mouse movement, and touch behavior to spot robotic or inconsistent activity.
By combining these signals, Ekho makes it extremely difficult for a fraudster to fake both a clean device and natural human behavior—even with stolen personal information.
Payment Signals Monitoring
Ekho closely monitors payment signals to catch fraud tied to stolen cards or fake bank accounts:
- Bank Account Verification: For ACH payments, we verify that the account belongs to the buyer. Mismatched names, newly opened accounts, or high-risk banks trigger alerts.
- Credit Card Checks: We use a fraud model to match the card details with network records. Mismatched ZIP codes, invalid CVVs, or stolen cards are flagged and blocked. Repeated card attempts or name mismatches raise suspicion.
- Payment Behavior Monitoring: We watch for rapid payment method changes, high-value transactions on new accounts, and multiple failed attempts—signs of stolen card testing.
- Ongoing Transaction Monitoring: Even after payment, we monitor for chargeback attempts and anomalies. With secure methods like vendor-guaranteed ACH, chargeback risk is minimal.
These checks ensure the buyer’s payment is legitimate and protect you from financial fraud.
Identity Verification & Document Checks
Ekho uses a robust KYC process to confirm each buyer’s identity is real and belongs to them:
- Government ID Verification: Buyers upload a valid photo ID during checkout. Ekho’s system automatically inspects security features (holograms, barcodes) and cross-checks extracted info (name, DOB, address) with what was entered.
- Database Validation: We validate ID numbers against trusted databases, including DMV or national registries when available. If the ID is invalid, altered, or linked to fraud, we halt the transaction immediately.
- Selfie & Liveness Checks: When needed, buyers provide a live selfie. We use biometric matching and liveness detection to ensure it’s the same person and not a spoof (e.g., photo of a photo).
- Additional Documents: For financing, we may request proof of income or address. These are checked for authenticity and consistency, e.g., matching names on utility bills.
- Email & Phone Verification: We verify contact info via confirmation codes and risk scores. Risky signals include new or disposable emails, virtual numbers, or contacts tied to fraud.
- SSN & Identity History: For financed deals, we verify SSNs and run identity history checks to flag links to past fraud or credit bureau alerts.
This layered verification ensures that only real, verified buyers make it through—blocking identity fraud before it can reach the dealership.
Watchlist and Blocklist Screening
Ekho enhances identity checks with powerful watchlist screening and a growing internal blocklist:
- Global Watchlists: Buyers are screened against government databases, including OFAC sanctions, PEP lists, and fraud/crime records. Flags on these lists result in a blocked sale and further review.
- Internal Blocklist: We track emails, phone numbers, devices, and addresses tied to past fraud. If a new buyer matches any of these, they’re flagged or auto-rejected—preventing repeat attempts by the same or related actors.
- Network & Velocity Analysis: We identify fraud rings by linking buyers with shared traits (e.g., same IP or phone number). Our system treats these as coordinated attempts and blocks them as a group.
- High-Risk Indicators: We maintain lists of risky emails, VoIP phone prefixes, and suspect patterns. If a buyer triggers multiple risk signals—like a fake email domain and unverified phone—they’re routed to manual review or rejected outright.
This system acts as a dynamic defense net, stopping known fraudsters from returning and improving with every blocked attempt.
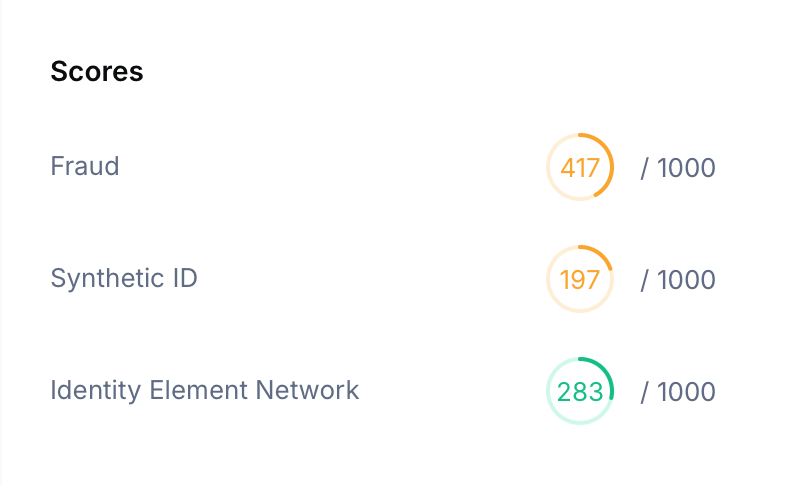
Fraud Dashboard & Risk Signals
Ekho uses a unified fraud dashboard to centralize all risk signals and enable fast, informed decisions on each and every deal.
- Risk Scoring: Each session is assigned a Risk Level (Low, Medium, High, Very High) based on real-time analysis of device data, identity verification, and payment behavior. A suspicious first-time user may show as “High,” while a returning, verified buyer may be “Low.”
- Signal Breakdown: Analysts can review detailed checks—email and phone risk levels, device and IP reputation, geolocation, verification status, and more. These sub-signals explain why a buyer is flagged, e.g., “SSN: owner deceased,” “Phone: unverified,” “Device: new,” “IP: proxy.”
- Fraud Investigation Tools: Analysts can view a buyer’s session history, device fingerprint, and linked activity across accounts, helping expose repeat fraud attempts under aliases.
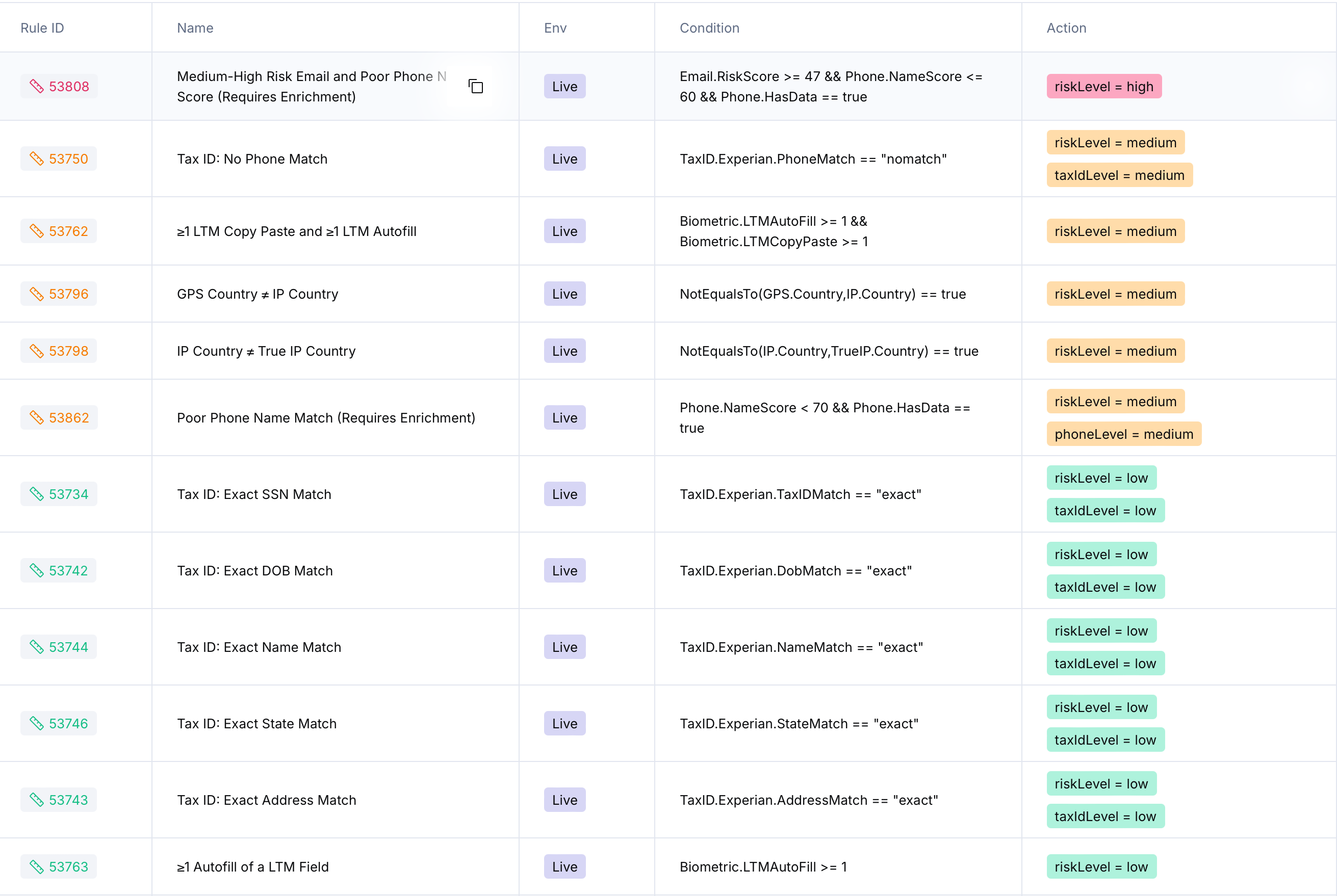
- Automated Rules & Alerts: Rules detect high-risk patterns (e.g., “$15K+ transaction on first order + risky email”) and trigger real-time alerts or auto-declines. New rules are added as fraud evolves.
- Case Management: For flagged buyers, the system creates cases with structured workflows—assigning analysts, logging reviews, and capturing outcomes to ensure no case is missed.
This dashboard provides a comprehensive risk snapshot for each order, ensuring only fully vetted buyers can progress towards order fulfillment.
Examples of Fraud Signals and Rules
Ekho’s fraud system tracks hundreds of signals to catch suspicious behavior early. Below are real examples that illustrate how our rules work and why certain activity is flagged:
- Suspicious emails: If a buyer uses an uncommon or disposable email domain (e.g. [email protected]), and it’s not found in public records or previous customer data, we raise the email risk. Fraudsters frequently rely on throwaway emails.
- Unverifiable phone numbers: Phones that don’t respond to SMS or are linked to VoIP services are flagged. While this alone might not block an order, it adds to the risk score when paired with other signals.
- Location mismatches: If a buyer claims to be in Texas but their IP is geolocated in another country or through a known proxy, we flag it. Rules like “billing state doesn’t match IP location” or “foreign IP with US shipping address” help identify spoofing attempts.
- Repeated attempts from the same device: If multiple buyer profiles originate from the same IP or device within a short period, we treat them as linked. A rule like “same device ID used by multiple accounts in 24 hours” can trigger auto-suspension and review.
- Unusual behavior during checkout: Completing an order extremely quickly, skipping steps, or attempting several large purchases in a short time can indicate automation or stolen credentials. Velocity rules monitor this, such as “more than two purchase attempts in one hour.”
- Payment red flags: Several failed payment attempts using different cards often signal stolen card testing. Similarly, bank accounts created recently or linked to high-risk financial institutions may be flagged before an ACH payment is accepted.
- ID and document inconsistencies: If the name on the uploaded ID doesn’t match the order details, or the photo clearly isn’t the buyer (or doesn’t match a required selfie), the system will immediately reject the transaction.
- Known fraud history: If any buyer details—email, phone, device—have been tied to previous fraud (internally or via third-party data), the system automatically assigns a very high risk level and often blocks the order outright.
- Delivery and geographic anomalies: Buyers requesting deliveries to addresses far from their billing address, or from out-of-state with mismatched driver’s licenses, are subject to extra verification. Rules like “shipping state doesn’t match ID state” help detect risky patterns.
These are just a sample of the kinds of inconsistencies our system looks for. Fraud often reveals itself through unnatural combinations of behavior, identity, and context. Ekho is built to catch these early and escalate appropriately.
Manual Review Process and Risk Tiers
While Ekho’s system automatically approves or blocks most transactions, some cases fall into a gray area and require human review. We assign each order a risk tier to determine the level of scrutiny:
- Low Risk: No red flags. Returning customer, verified contact info, clean ID, normal behavior. These orders are automatically approved and move straight to processing. Dealers usually won’t notice anything unusual here.
- Medium Risk: Some minor inconsistencies—like a new email or unverifiable address—but no clear fraud. These cases may trigger an extra verification step (e.g., utility bill upload), or a quick manual check by our fraud team. Most are resolved quickly and move forward.
- High Risk: Significant red flags, such as failed ID verification or a blocklist match. These are paused for full manual review. An analyst inspects all risk signals, and if needed, escalates to a senior reviewer. Most high-risk cases end in rejection due to confirmed fraud or unresolved discrepancies.
- Very High Risk: Severe and conclusive fraud signals—such as a stolen ID combined with a blocklisted device. These are automatically declined..A post-review confirms the call, but action is immediate.
Manual Review Tiers

- Tier 1 Review: Fast review by support staff for medium-risk cases—verifying a few details or requesting clarification.
- Tier 2 Review: Deep-dive investigation by senior analysts for high-risk cases—leveraging internal tools, third-party data, and fraud expertise.
By the time an order is marked Cleared for Delivery, it has either passed all automated checks or been carefully reviewed by our team. This layered system ensures real buyers aren’t delayed, and suspicious ones never slip through.
Dealer Guidance: Final Fraud Checks at Fulfillment
Ekho screens buyers thoroughly, but as the dealer, you provide the final line of defense during handoff or delivery. We equip you with verified buyer information so you can confidently confirm identity before releasing the vehicle. If you’re interested in supplementing our fraud efforts, here are some effective measures you can take:
- Match the Buyer’s ID in Person: At fulfillment time, ask to see the physical ID the buyer uploaded. Confirm the name matches your documents and the photo matches the person. You can reference the ID image in the Ekho platform for comparison. If anything seems off—wrong ID, no ID, or mismatched photo—pause the handoff and contact Ekho immediately.
- Quick Secondary Identity Check: For high-value transactions, consider a quick real-time check. Call or text the phone number on file while the buyer is present. You can also ask a casual verification question from their application (like their ZIP code). These simple checks are highly effective.
- Review Any Additional Documents: If Ekho provided supporting documents (e.g., utility bill, insurance), verify the originals if available. Look for name and address consistency across all materials, especially in financed deals.
- Watch for Evasive Behavior: If a buyer seems rushed, nervous, or avoids engagement, take note. Asking for a quick delivery photo is both a deterrent and a useful verification step—many dealers do this as a standard practice.
- Confirm Delivery Address: For vehicle delivery, ensure the destination matches the address used in checkout or on the buyer’s ID. Be cautious of last-minute changes and verify any new instructions with Ekho support before proceeding.
- Contact Ekho If Anything Feels Off: If something doesn’t seem right—even if you’re unsure—pause the delivery and reach out. Our fraud team can assist immediately with re-verification or guidance.
These checks rarely catch issues, but when performed consistently, they can add an extra layer of protection. Together, we can ensure vehicles go only to legitimate buyers.  Ekho’s fraud detection is methodical and multi-layered—we check several facets of a buyer’s information and behavior in parallel. Below are the key elements of our process and how each works:
Ekho’s fraud detection is methodical and multi-layered—we check several facets of a buyer’s information and behavior in parallel. Below are the key elements of our process and how each works:



